HOWTO: Enabling HTTPS support on an ISA server
Print
ZTN2019
ID: ZTN2019
This Zetalink technical note applies to:
- Zetalink version 1.0
- Microsoft Internet Security and Acceleration server 2000
- Microsoft Internet Information Services server version 5.0
Summary
This document details step-by-step instructions to allow secure access to the Zetalink External Website through Microsoft Internet Security and Acceleration (ISA) server, using a Secure Sockets Layer (SSL) server certificate. It assumes that you have followed the steps in the Zetalink Implementation Guide to install the Zetalink External Website components on an Internet Information Services (IIS) server within the corporate network.
More information
SSL bridging refers to the ability of ISA server to encrypt or decrypt client requests and pass on the request to a destination Web server.
SSL bridged connections actually involve two connections:
- From the client to the external interface of the ISA server is one SSL session.
- From the internal interface of the ISA server to the internal Web server is another SSL session.
You may decide to use one or both of these to secure the Zetalink External Website. The instructions below will allow for both connections to be encrypted.
Creating the Certificate Request
This step and the next can be skipped if you have already obtained a certificate from a trusted "Certifying Authority" (CA) such as Verisign. If not follow these steps to acquire one.
Note: Zetalink only supports HTTPS with security certificates issued by a trusted root CA. This is due to most WAP gateways not offering a facility to accept security certificate prompts from untrusted sources.
- Log on to the IIS server and open the Internet Services Manager snap in.
- Double click the server name to expose all the websites.
- Right click the Website hosting the Zetalink virtual directory (this will usually be the Default Web Site) and choose 'Properties'.
- Go to the 'Directory Security' tab.
- Click 'Server Certificate' and select 'Next' on the Welcome screen.
- Choose 'Create a new certificate' and select 'Next'.
- Select 'Prepare the request now, but send it later' and click 'Next'.
- Enter the certificate name. The certificate name should match the host and domain being published. This is the name the user will type into their mobile device (e.g. www.domain.com).
- Select the 'Bit Length' desired (1024 is recommended) and click 'Next'.
- Enter the 'Organization' and 'Organizational unit' (e.g. company name and department) then click 'Next'.
- Enter the Site's 'Common Name'. This should be the same as the certificate name in step 8. Click 'Next'.
- Enter your Geographical Information and click 'Next'.
- Enter the certificate request file name and path (default is fine). This is the 'Certificate Signing Request' (CSR)
- Confirm the details you have entered and select 'Next' on the Request File Summary dialog.
- Select 'Finish' to close the Web Server Certificate Wizard.
- Then select 'OK' to close the Web Properties.
Submitting the Certificate Request
The process described below may change between CA's, but at the end of the process you should receive an e-mail from them containing the server certificate.
- Launch the browser on the IIS server and point it to the certificate server (e.g. http://www.verisign.com), navigate to the Secure Site Services section and select the certificate you wish to purchase.
- Follow the instructions presented until you reach the 'Submit CSR' page.
- Paste the contents of the CSR created above (e.g. c:\CERTREQ.TXT if the default was chosen) into the area. Make sure you include the BEGIN and END headers in the request. The content will look similar to this:
-----BEGIN NEW CERTIFICATE REQUEST-----
MIIDMzCCApwCAQAwWDERMA8GA1UEAxMIZ2FuZGVyMmsxDDAKBgNVBAsTA2ZmZjEL
MAkGA1UEChMCZmYxDDAKBgNVBAcTA2RzZDENMAsGA1UECBMEZGRzZDELMAkGA1UE
BhMCVVMwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAJXabzY5dRyHiHC+zujL
rhBRcwW7kQBt3JiWZOPMjlBCmlhYMKQ5o63IR3SaOpXGnwqgC3fbIZP5Bf3h5grq
LiRc+xVBjRmycqPvE1CiPwrWr9DglG4XPOApcmCP159bTaxkI7z/5seqPgX+Bt4/
/w8wKN8SB6Fop4A4X3iG5kEVAgMBAAGgggGZMBoGCisGAQQBgjcNAgMxDBYKNS4x
LjI2MDAuMjB7BgorBgEEAYI3AgEOMW0wazAOBgNVHQ8BAf8EBAMCBPAwRAYJKoZI
hvcNAQkPBDcwNTAOBggqhkiG9w0DAgICAIAwDgYIKoZIhvcNAwQCAgCAMAcGBSsO
AwIHMAoGCCqGSIb3DQMHMBMGA1UdJQQMMAoGCCsGAQUFBwMBMIH9BgorBgEEAYI3
DQICMYHuMIHrAgEBHloATQBpAGMAcgBvAHMAbwBmAHQAIABSAFMAQQAgAFMAQwBo
AGEAbgBuAGUAbAAgAEMAcgB5AHAAdABvAGcAcgBhAHAAaABpAGMAIABQAHIAbwB2
AGkAZABlAHIDgYkAqhB90KaT+xMLs+qIeBFFzGynaongHG0OdohUl6kP59cQLRKV
VH4yDN3sa+NhIcmJa5Ve3KVCm0q/3kOnP4Y4lItexKb5XgQVdAZBVrFsyaEocdAZ
jirw5yiDTUAtycmvjDf7fWscrgsHVGCYi4JTZ43AS0sS/+oaL1zQy7gi4DAAAAAA
AAAAADANBgkqhkiG9w0BAQUFAAOBgQBq39Uotiiyc+ZpBvRHyeKoCx9XKDnaVSm6
nNJGRlCo8kdLWMpOMK7teTiDOOLJ3aiHN4U6QG5GFSLfdkTq4DxgK3Rbcl9qaKFI
p2ZUQVfwxTALAwVnO3m7BVgmDnTMkbc9KSHKUtwDYHOXcrk1OOmbUG4HZnB4eLo8
HwSJGy676w==
-----END NEW CERTIFICATE REQUEST-----
- Submit this request and provide the additional contact information that allows the CA to perform checks in order to issue the certificate.
Note: It may take several days for the CA to issue a certificate. It will usually be received by e-mail to the address you provided in the above submission.
- Once the server certificate is received save the *.CER to disk and continue below.
Installing the issued certificate
- Log on to the IIS server and open the Internet Services Manager snap in.
- Double click the server name to expose all the websites.
- Right click the Website you created the certificate request for and choose 'Properties'.
- Go to the 'Directory Security' tab.
- Click 'Server Certificate' and select 'Next' to continue.
- Choose 'Process a pending request and install the certificate' and select 'Next'.
- Enter the path to the certificate from the CA you saved to disk earlier in step 5 ("Submitting the Certificate Request" section above) and click 'Next'.
- Verify the information is correct on the 'Certificate Summary' screen and click 'Next'.
- Click 'Finish' to complete the process.
Setting up the SSL Website
- Right click the Website you added the certificate to and choose 'Properties'
- On the 'Web Site' tab confirm the 'SSL port' is set to 443 (default). You can use a different port if you wish and later set ISA to match this port.
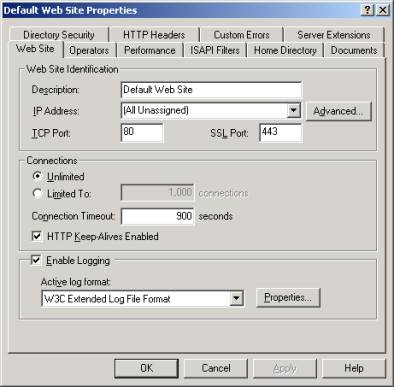
- Click OK twice to close the Web Properties.
- If you only want Zetalink to accept SSL connections (only HTTPS not HTTP), right click the Zetalink virtual directory and select 'Properties'.
- Go to the 'Directory Security' tab and click 'Edit' in the 'Secure communications' section.
- Check the 'Require secure channel (SSL)' box.
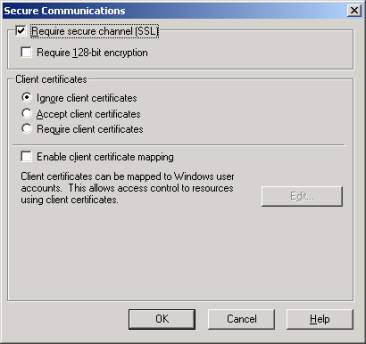
- Click OK twice to close the Zetalink Properties.
At this point make sure you can establish an HTTPS session to the Zetalink External Website from the ISA server with your browser. Enter the URL as https://www.domain.com/Zetalink/test.htm (where www.domain.com is the name of the certificate) confirm the test page is displayed and the browser padlock reports the bit strength of the CA issued certificate. Make sure the ISA server can resolve this name to the IIS servers IP address. You may have to create a HOST file locally on the ISA server to resolve the IP address.
Export the certificate from the IIS server
This step is required in order to import the server certificate into the certificate store on the ISA server and allow it to host websites using the SSL protocol.
Note: You must export the certificate with the associated private key. If you do not have this key the ISA server will not allow you to use this certificate for SSL.
- Open a blank Microsoft Management Console (MMC) on the IIS server.
- Add the Certificates snap-in for the 'Computer Account' on the 'Local Computer'.
- Expand Personal/Certificates and right click on the certificate issued from the CA, then select 'All Tasks' then 'Export'.
- Select 'Next' on the Welcome wizard.
- Select 'Yes, export the private key' and select 'Next'.
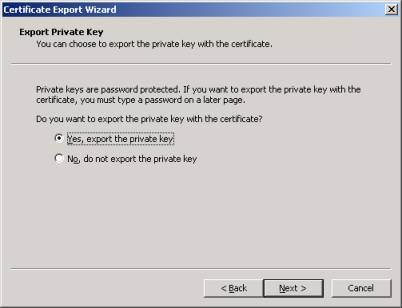
Note: If you do not see this option, the private key has already been exported to another computer or it never existed on this computer. You cannot use this certificate on the ISA server, you must request a new certificate for use with the ISA server or locate the computer where the private key exists.
- Leave the defaults on the 'Export File Format' dialog and select 'Next'.
- Enter a password for the certificate and click 'Next'.
- Enter a file name and select 'Next' (e.g. certpvt).
- Note the location of the exported certificate and select 'Finish' to complete the wizard.
Import the certificate on the ISA server
- Open a blank Microsoft Management Console (MMC) on the ISA server.
- Add the Certificates snap-in for the 'Computer Account' on the 'Local Computer'.
- Expand 'Personal' and right click 'Certificates', select 'All Tasks' then 'Import '.
- Select 'Next' on the Welcome wizard.
- On the 'File to import' dialog, browse to the exported certificate in step 9, "Export the certificate from the IIS server" section and select 'Next'.
- Enter the password and select 'Next'.
- Leave the defaults to place the certificate in the Personal store and select 'Next'.
- Select 'Finish' to complete the wizard.
Enable certificate for incoming web requests
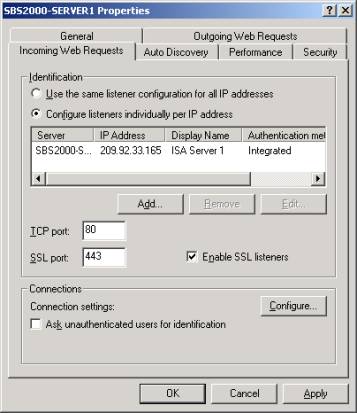
- Open the ISA Management snap-in and expand Servers and Arrays.
- Right click the name of the ISA server and select 'Properties'.
- Select the 'Incoming Web Requests' tab and select 'Add'.
- Select the ISA server name and the IP address of the external interface.
- Check the 'Use a server certificate to authenticate to web clients' and click 'Select'.
- Select the Imported certificate and click OK.
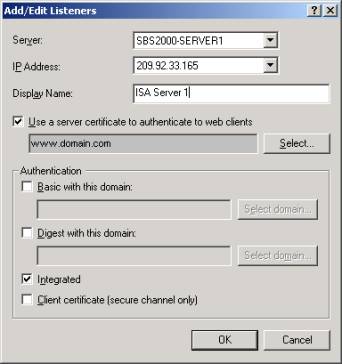
- Select OK to close the 'Add/Edit Listeners' dialog.
- Check to 'Enable SSL listeners', enter the 'SSL port' (443 by default) and click OK to close.
Create the ISA Destination Sets
- Navigate to Policy Elements/Destination Sets, then right click and select 'New' then 'Set'.
- Enter a descriptive name for the destination set, then click 'Add'.
- Enter the name of the 'Destination'. This needs to be the name of the published website (e.g. www.domain.com) and also the name of the certificate.
- Enter the 'Path' to the Zetalink virtual directory as:
/Zetalink/*
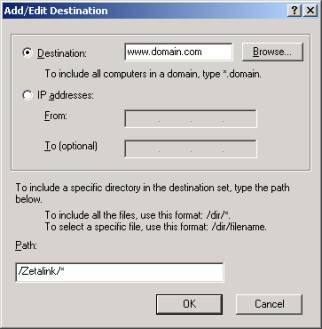
- Click OK and OK again to close the 'Destination Set' dialog.
Create the Web Publishing rule
- Select Publishing/Web Publishing Rules, right click and select 'New' then 'Rule' to launch the Web Publishing Rule Wizard.
- Give the rule a descriptive name.
- Select 'Apply this rule to:' "Specified destination set" and for 'Name:' select the destination set created above. Click 'Next'.
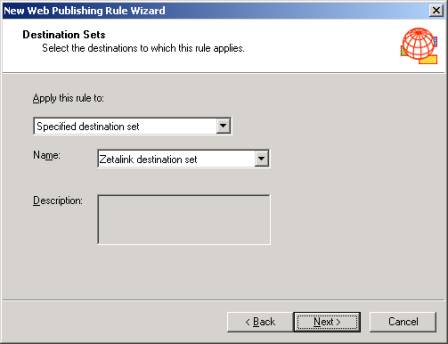
- Select the appropriate 'Client Type'.
- On the 'Rule Action' window select 'Redirect the request to this internal Web server (name or IP address):'
- Make sure you enter the name of the Website being published (not the IP address or NETBIOS name). This is the same as the certificate. Be sure not to check "Send the original host header to the publishing server instead of the actual one (specified above), by leaving this blank we are telling the ISA server to use the FQDN that we have specified.
Note: Make sure the ISA server can resolve this name to the IIS servers IP address. The external DNS servers will resolve the published Website name to the external IP address of the ISA server but the ISA server needs to resolve the name to the internal published IIS server. You may have to create a HOST file locally on the ISA server to resolve the IP address.
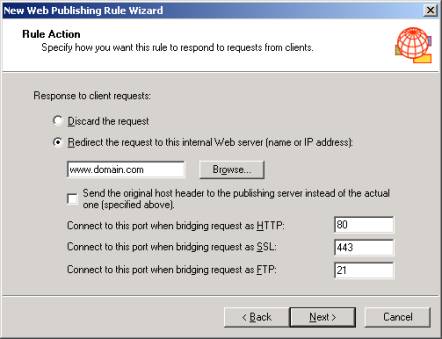
- Click 'Next' and then 'Finish' to complete the wizard.
- Use the Services snap-in to restart the 'Microsoft Firewall' and 'Microsoft Web Proxy' services.
At this point you should be able to enter the URL 'https://www.domain.com/Zetalink/go.asp' from WAP mobile device and successfully login to Zetalink.
Troubleshooting
When attempting to access the URL: https://www.domain.com/Zetalink/test.htm from a browser on the ISA server, you receive the error:
The page cannot be displayed.
Cannot find server or DNS Error.
This is a generic error message, however the most likely cause in this scenario is a name resolution one. To verify this, attempt the URL again, but this time replace the certificate name with the NETBIOS name of the IIS server (e.g. https://server_name/Zetalink/test.htm). If this returns the Zetalink test page correctly, add an entry in the ISA server's HOST file that maps the IP address of the IIS server to the certificate name. If the test page is not displayed, review this document again and confirm you have not missed any steps.
Whilst enabling the certificate on the ISA server for incoming web requests you receive this error:
There are no certificates configured on this server.
You have either not yet imported the certificate you exported from the IIS server or you imported a certificate that does not contain the private key. Review sections "Export the certificate from the IIS server" and "Import the certificate on the ISA server" above to rectify this.
Note: You will need to reopen the ISA Management snap-in once you have imported the certificate with a private key, to clear this message.
References
ZTN2020-HOWTO Enabling HTTPS support on an IIS web server
ZTN2021-HOWTO Configuring Microsoft ISA Server with Zetalink
ZTN2022-HOWTO Configuring Zetalink to only allow HTTPS access
Last updated: 23 November 2001 (GC/DH)